
How IoT is Revolutionizing Agriculture: Key Innovations and Future Prospects
Discover how IoT is transforming traditional farming through key innovations, real-world success stories, and future trends that are shaping the agricultural sector.
Promises and threats of a disruptive technology
The world of IoT is massive and in constant growth. As we stand in 2024, the number of IoT devices around the globe has skyrocketed. Current estimates show that there are more than 17 billion devices connected worldwide. This number is expected to rise, underscoring how deeply technology is woven into our everyday lives. Take healthcare, for instance, where IoT is widely used for monitoring patients and managing devices. About 70% of healthcare organizations now employ IoT for operational purposes. Similarly, in the industrial area, what’s known as the Industrial Internet of Things (IIoT) is transforming manufacturing and automation processes.
In this article, we explore the dynamic connection between IoT and 5G, focusing on the security challenges and advancements this combination brings.
The first generation mobile network (1G) was all about voice. 2G was about voice and texting; 3G was about voice, texting, and data; 4G was a faster 3G, and 5G will be even faster; it will be fast enough to download a full-length HD movie in seconds.
With the arrival of 5G, it looks like the foundation for realizing the full potential of IoT is finally here.
As of October 2023, there were around 1.9 billion 5G subscriptions globally, according to the latest Ericsson Mobility Report. While Asia Pacific remains a key driver of growth, with China alone boasting over 341 cities with 5G coverage, the exact regional percentage of 5G subscriptions requires constant monitoring due to rapid market changes.
While lightning-fast downloads are impressive, 5G’s true potential lies in its unique combination of high speed, ultra-low latency (down to 1 millisecond), and widespread coverage (expected to reach 85% of the global population by 2029 as per Ericsson projections.
However, 5G is much more than just fast downloads; its unique combination of high-speed connectivity, very low latency, and ubiquitous coverage will support smart vehicles and transport infrastructure such as connected cars, trucks, and buses, where a split second delay could mean the difference between a smooth flow of traffic and a terrible car crash.
As per Siemens estimates, 5G can potentially boost manufacturing productivity by up to 20%. Healthcare is also expected to benefit significantly from 5G, especially in regard to remote surgery, real-time diagnostics, and improved patient monitoring. According to a McKinsey & Company report, 5G could enable up to $500 billion in annual healthcare savings by 2025.
On top of that, 5G is expected to give a boost to AR/VR experiences thanks to faster data transfer and reduced lag. The global AR & VR Market is expected to reach $300.3 billion by 2024, showcasing the growing demand for enhanced immersive experiences.
By 2024, the IoT world has seen substantial growth, with a multitude of devices seamlessly integrating into our everyday lives. Take the healthcare sector, for instance, where IoT devices have become indispensable. IV pumps, patient monitors, and glucometers are just a few examples that underscore the deep integration of IoT in daily healthcare routines, demonstrating its pivotal role in patient care.
The Industrial Internet of Things (IIoT) harnesses the power of IoT to create intelligent machines capable of autonomous communication and decision-making. This evolution towards smart factories forms a vital component of the larger paradigm shift known as Industry 4.0. Technologies such as IoT, AI, and big data are driving forces behind this manufacturing revolution. Consider Germany, where a striking 84% of manufacturers aim to invest a substantial €10 billion (approximately $10.52 billion) annually in IoT solutions by 2025. This broad adoption underscores the transformative and significant impact of IoT in industrial settings.
5G technology represents the newest cellular technology advancement, designed to boost wireless networks’ speed and responsiveness significantly. With 5G, wireless broadband connections could achieve speeds up to 20 Gbps, according to some estimates, faster than wired networks and offer ultra-low latency of 1 millisecond or less for real-time applications. Thanks to its broader bandwidth and complex antenna technology, 5G is tailored to accommodate a substantial increase in data transmission over wireless systems.
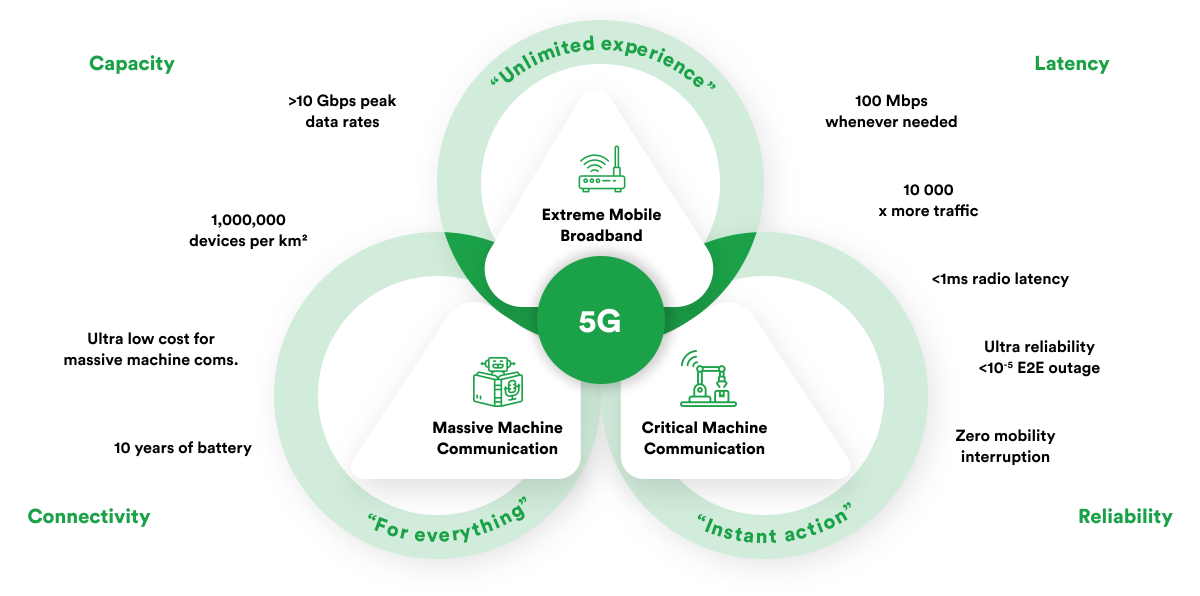
The nature of 5G networks also poses specific challenges. The arrival of 5G technology marks a significant shift in digital connectivity, bringing advancements far surpassing its predecessors and set to revolutionize our interaction with the internet. One of its standout features is supporting over a million devices per square kilometer, a crucial factor for the promising Internet of Things networks. Additionally, 5G features peak data rates that exceed 10 Gbps, enabling incredibly high-speed mobile broadband.
A key attribute of 5G is its ultra-low latency, less than one millisecond, which opens doors for real-time, critical machine-type communications. Furthermore, its ultra-reliability, with almost zero end-to-end outages, guarantees consistent connectivity, which is essential for mission-critical applications. These combined features lay the foundation for a new digital transformation era, positioning 5G as a central player in the evolution of interconnected devices and services.
The merger of IoT and 5G technology is a key element in the evolution of modern tech. The high-speed, low-latency nature of 5G is ideally suited to meet the demands of an extensive IoT network. It provides the required bandwidth and speed to manage the data from billions of IoT devices. This synergy is opening exciting new possibilities across various sectors. In smart cities, for instance, 5G can significantly boost IoT applications in areas such as traffic management, public safety, and environmental monitoring, offering real-time data analysis and enhancing city services.
In healthcare, IoT and 5G drives progress in telemedicine and patient monitoring. It enables the real-time transmission of data, which can be crucial in saving lives. The increasing number of IoT devices in healthcare, which is expected to generate up to $108.60 billion in revenue by 2024, underscores the vast potential of this integration. In agriculture, IoT devices used for monitoring crop health, soil conditions, and weather can be significantly improved with the capabilities of 5G, leading to more efficient and productive farming practices.
Integrating IoT devices with 5G networks significantly expands the field for potential cyber threats. As the number of connected devices skyrockets, so does the potential for vulnerabilities. Each IoT device, ranging from smart home thermostats to industrial sensors, could be a gateway for cyberattacks. In 2022, the number of IoT cyber-attacks rose to over 112 million, dramatically increasing and underscoring the growing security challenge. This increase in cyber threats is mainly due to the variety and sheer number of devices connected, many of which may lack strong security protections.
The healthcare sector is particularly at risk with its widespread adoption of IoT for patient monitoring and device management. Notably, 82% of healthcare organizations using IoT devices reported experiencing a security breach within a year and a half, illustrating the heightened risk environment due to the spread of IoT devices. These security breaches pose threats not only to sensitive patient data but also disrupt essential healthcare services.
As IoT devices constantly gather, send, and process enormous amounts of data, concerns about data privacy become increasingly crucial. The IoT environment often involves handling sensitive personal and business information, including health records, financial details, and private conversations. The interconnectedness of these devices heightens the risk, as the compromise of even a single device in the network can result in the unintended disclosure of private information.
For example, IoT devices collect and send highly sensitive patient data in the healthcare sector. Ensuring the security of this data is not only a privacy issue but also a legal necessity, especially for healthcare providers who must comply with regulations like HIPAA in the United States. In industrial settings, IoT devices gather data that could uncover proprietary business methods or confidential information. Exposure to such data can lead to substantial competitive disadvantages.
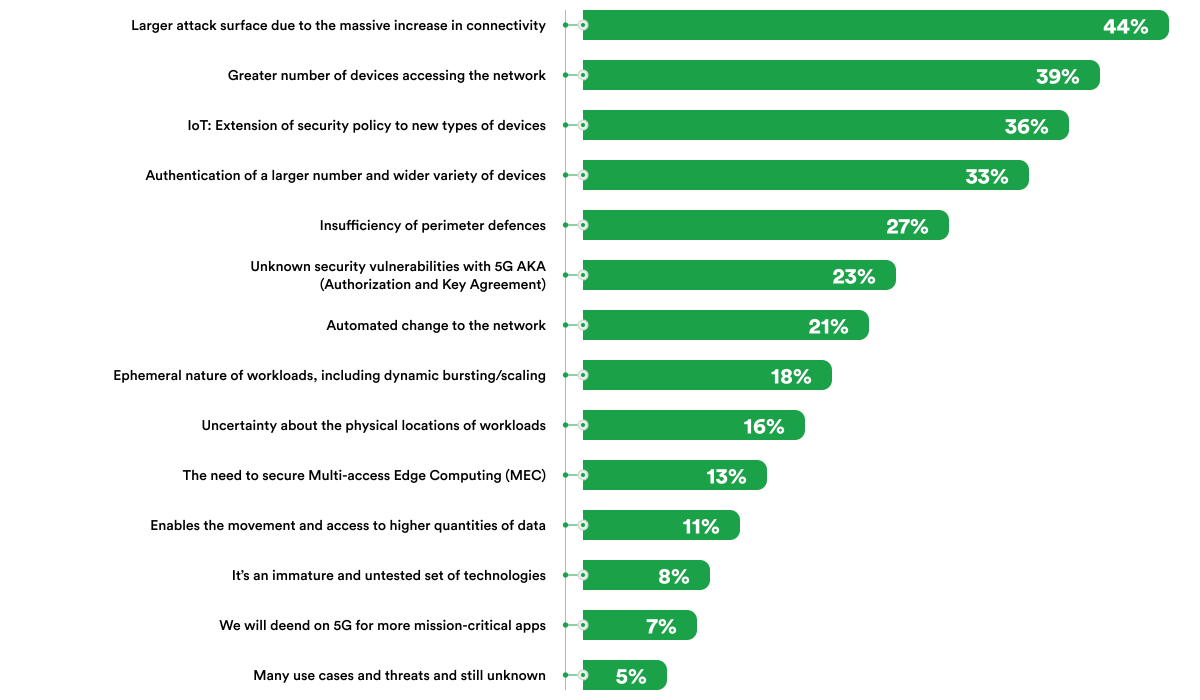
While 5G networks significantly improve speed and connectivity, they also introduce new security risks from the network’s structure and the vast array of devices they support. The primary concern for many industry professionals is the expanded attack surface resulting from increased connectivity. Another key issue is the authentication of a diverse and growing array of devices, highlighting the complexity of managing and securing these devices’ identities within the 5G network.
A particular area of concern in 5G networks is using outdated operating systems in IoT devices. An example is in medical imaging devices, where 83% were found to be running on unsupported operating systems, leaving them open to malware and other cyber threats. This risk is especially troubling, considering these devices’ essential role in healthcare.
The inherent nature of 5G networks also presents unique challenges. Unlike earlier mobile network generations, 5G networks are largely software-based and utilize network function virtualization. If not adequately secured, these aspects can lead to vulnerabilities. Moreover, the decentralized structure of 5G networks, with increased data processing at the edge, opens new potential security gaps for attackers to exploit.
The advancements in IoT security, bolstered by the introduction of 5G technology, are a leap forward in addressing the intricate security requirements of various IoT systems, from smart grids to healthcare monitoring devices. The integration of 5G enhances the security architecture of these systems, providing a more robust and secure communication framework.
5G technology brings to the table superior security features for IoT networks, such as advanced encryption methods, improved identity management, and sophisticated privacy-preserving tactics. These enhancements are critical for protecting data integrity and confidentiality across the network.
With the rollout of 5G, there has been a significant development in IoT security protocols and standards, specifically designed to leverage 5G’s strengths. These include enhanced authentication and authorization processes, ensuring that only authorized devices and users can access the network.
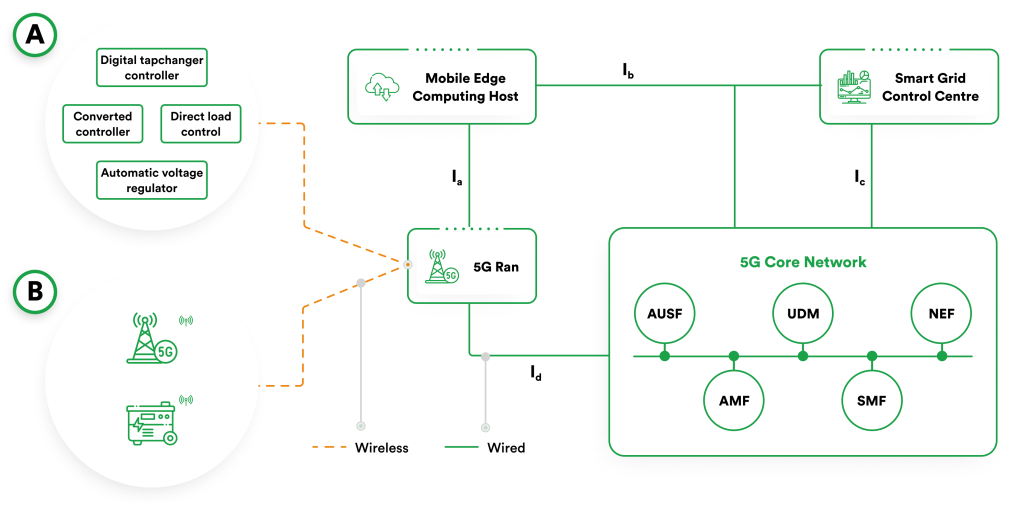
A prime example of 5G’s impact on IoT security is the integration of smart grid systems with 5G networks. This combination results in a secure, responsive infrastructure capable of managing complex energy distribution and control systems. Smart grids, when equipped with 5G, benefit from its high-speed, low-latency, and extensive connectivity, enhancing real-time data communication between components like renewable energy sources, automated fault detectors, and distribution automation controllers. The advanced encryption and network slicing capabilities of 5G safeguard operational data, making grids more resilient to cyber-attacks.
Additionally, the integration of Mobile Edge Computing (MEC) within these systems is pivotal. MEC allows for local, real-time data processing, thereby sharply reducing reaction times to security threats. This not only bolsters security but also elevates the efficiency and reliability of the energy network.
The convergence of IoT and 5G is not limited to smart grids. In healthcare, 5G enables secure, real-time monitoring of patient data through IoT devices, offering enhanced privacy and reliability in sensitive health information transmission. In the industrial sector, 5G’s role in securing IoT-driven industrial automation and control systems is pivotal, providing a shield against industrial espionage and cyber threats.
As we look into the future of IoT security within the 5G landscape, several critical areas stand out as key for further development and innovation.
There’s a clear trend towards integrating Artificial Intelligence and Machine Learning more deeply into IoT and 5G security. These technologies are poised to play a crucial role in predictive analytics, enabling the early detection and neutralization of potential security threats. Another emerging trend is adopting blockchain technology for decentralized security in IoT, which could diminish the risks of centralized vulnerabilities and boost data integrity across networks.
Continued R&D efforts are essential for advancing IoT security in the 5G era. This includes developing more robust encryption methods, exploring new security protocols tailored for the vast and varied landscape of IoT devices, and innovating in the field of quantum-resistant cryptography to prepare for the post-quantum computing age. Furthermore, as 5G networks evolve, research into securing the more dynamic network topologies and the potential vulnerabilities introduced by network slicing will be critical.
The future will also see a greater emphasis on policy and regulatory measures to govern the security of IoT in the 5G era. This includes formulating international standards for IoT security, establishing clear guidelines for data protection in the age of massive IoT data generation, and ensuring compliance across different jurisdictions. Governments and regulatory bodies must collaborate with industry experts to keep pace with the rapid evolution of technologies and the corresponding security requirements.
As the ecosystem of connected devices continues to grow exponentially, there will be challenges and opportunities in securing the IoT landscape. On the one hand, the sheer scale of connectivity poses significant security challenges; on the other, this connectivity offers a wealth of data that, if harnessed correctly, can strengthen security postures. The opportunity lies in leveraging the full potential of 5G to support sophisticated IoT applications while maintaining a secure and trustworthy environment.
The arrival of 5G marks a significant turning point in IoT security, introducing new possibilities and challenges. 5G’s enhanced features, such as higher bandwidth and reduced latency, are pivotal in advancing IoT applications. However, these advancements also call for more robust security measures. Advanced security protocols and state-of-the-art encryption technologies must complement the improvements in connectivity and the growing number of devices. As these numerous devices become more integrated into our daily routines, a solid commitment to upholding strong security standards is essential.
Creating a secure IoT environment demands a collaborative approach involving technology providers, regulatory bodies, and users. This joint effort is crucial to harnessing the benefits of IoT fully and responsibly. As we navigate the intricate web of emerging technologies, finding the right partner who understands the complexities and nuances of IoT security becomes paramount. Our collective diligence and adaptability will determine the future of IoT security in the 5G era to emerging threats. By adhering to these principles, we can confidently move forward in this evolving digital landscape, ensuring that our interconnected world remains resilient and reliable.

Discover how IoT is transforming traditional farming through key innovations, real-world success stories, and future trends that are shaping the agricultural sector.

Delving into the IoT device onboarding requirements, challenges and implementation best practices across smart home, industrial, and healthcare settings.

Delving into the complexities of AIoT, exploring its core principles, current state, challenges, and future trends.
Copyright © 2023 rinf.tech. All Rights Reserved.
Terms & Conditions. Cookie Policy. Privacy Policy.
Politica Avertizari de Integritate (RO)