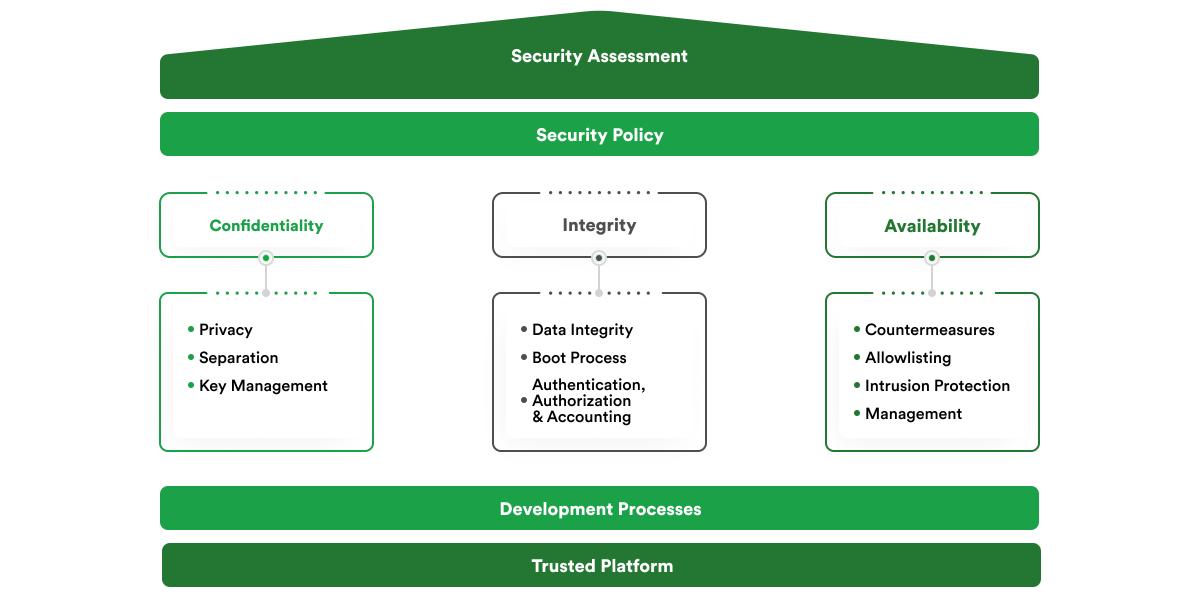
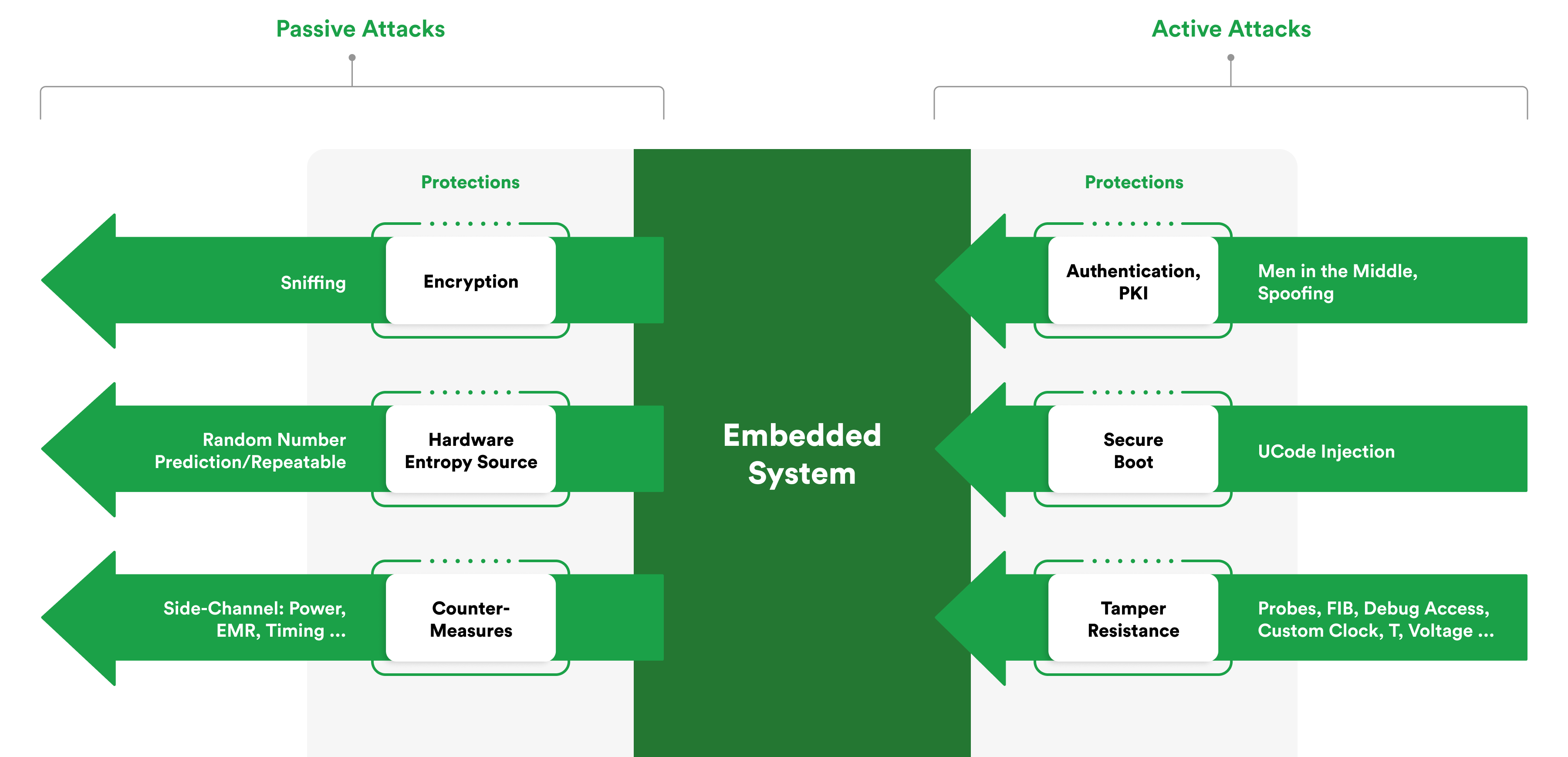
A comprehensive, multi-layered approach is essential in addressing the complex security challenges inherent to embedded systems. This strategy must be holistic, encompassing technical measures and procedural and organizational practices to fortify these systems against a spectrum of threats.
Security-by-Design
At the forefront of these strategies is the principle of Security-by-Design, which requires the integration of security considerations from the earliest stages of system design and development. This proactive approach ensures that security is not retrofitted as an afterthought but is embedded into the DNA of the system, addressing potential vulnerabilities before deployment. The concept of Security-by-Design is supported by industry standards and guidelines, such as those from the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST), which offer frameworks for embedding security into the software development lifecycle.
Risk Assessment
Conducting thorough risk assessments forms the backbone of effective security strategy for embedded systems. This process involves identifying potential threats, assessing vulnerabilities, and evaluating the impact of potential breaches on the system’s functionality and the data it handles. By understanding the risk landscape, developers and engineers can prioritize security measures, focusing resources on mitigating the most critical vulnerabilities. Tools and methodologies for risk assessment, such as the Common Vulnerability Scoring System (CVSS) and threat modeling, provide structured approaches for evaluating and managing risks.
Robust Security Architecture
The architecture of embedded systems must be robust and resilient, capable of defending against attacks and ensuring the integrity and confidentiality of data. Implementing strong encryption for data at rest and in transit, employing secure authentication mechanisms, and providing fast boot processes are fundamental components of this architecture. Encryption algorithms, such as AES (Advanced Encryption Standard), and secure communication protocols, like TLS (Transport Layer Security), are crucial for protecting sensitive information. Furthermore, hardware-based security features, such as Trusted Platform Modules (TPMs) and Hardware Security Modules (HSMs), can enhance the security of embedded devices by providing secure storage for cryptographic keys and supporting specific boot mechanisms.
Secure Coding Practices
Secure coding practices are another vital strategy in mitigating vulnerabilities within embedded systems. This involves adhering to coding standards that minimize the risk of introducing security flaws, such as buffer overflows, injection attacks, and other exploit vectors. Organizations such as the Open Web Application Security Project (OWASP) and the Software Engineering Institute (SEI) at Carnegie Mellon University offer guidelines and best practices for secure coding. Regular code reviews, static and dynamic analysis, and automated tools can help identify and rectify security flaws during the development process.
Network Segmentation and Monitoring
Network segmentation and monitoring are pivotal in securing embedded systems, particularly those integrated into more extensive networks or the Internet of Things. By segmenting networks, organizations can isolate critical systems and minimize the potential impact of a breach. Continuous monitoring of network traffic and system behavior enables the early detection of anomalous activities that may indicate a security incident, facilitating prompt response and mitigation.
Regular Updates and Patching
Regular updates and patching are critical for maintaining the security integrity of embedded systems throughout their operational lifespan. Despite the challenges associated with updating devices that are often resource-constrained and deployed in inaccessible locations, mechanisms for secure and reliable firmware updates are essential. This may involve over-the-air (OTA) update mechanisms that ensure the authenticity and integrity of updates through cryptographic signatures.